Yet another Tech Support Scam
March 19, 2024
Originally posted on CheckPhish Community
Introduction
While researching another phishing attack using urlscan, I inadvertently stumbled upon a typical tech support scam. The 'similar' tab revealed almost 200 similar template websites at the time, which has now grown to over 500. It is concerning that new domains are being registered daily despite numerous complaints lodged against them. This topic aims to share my experience in detecting and combating a prolific scam operation.
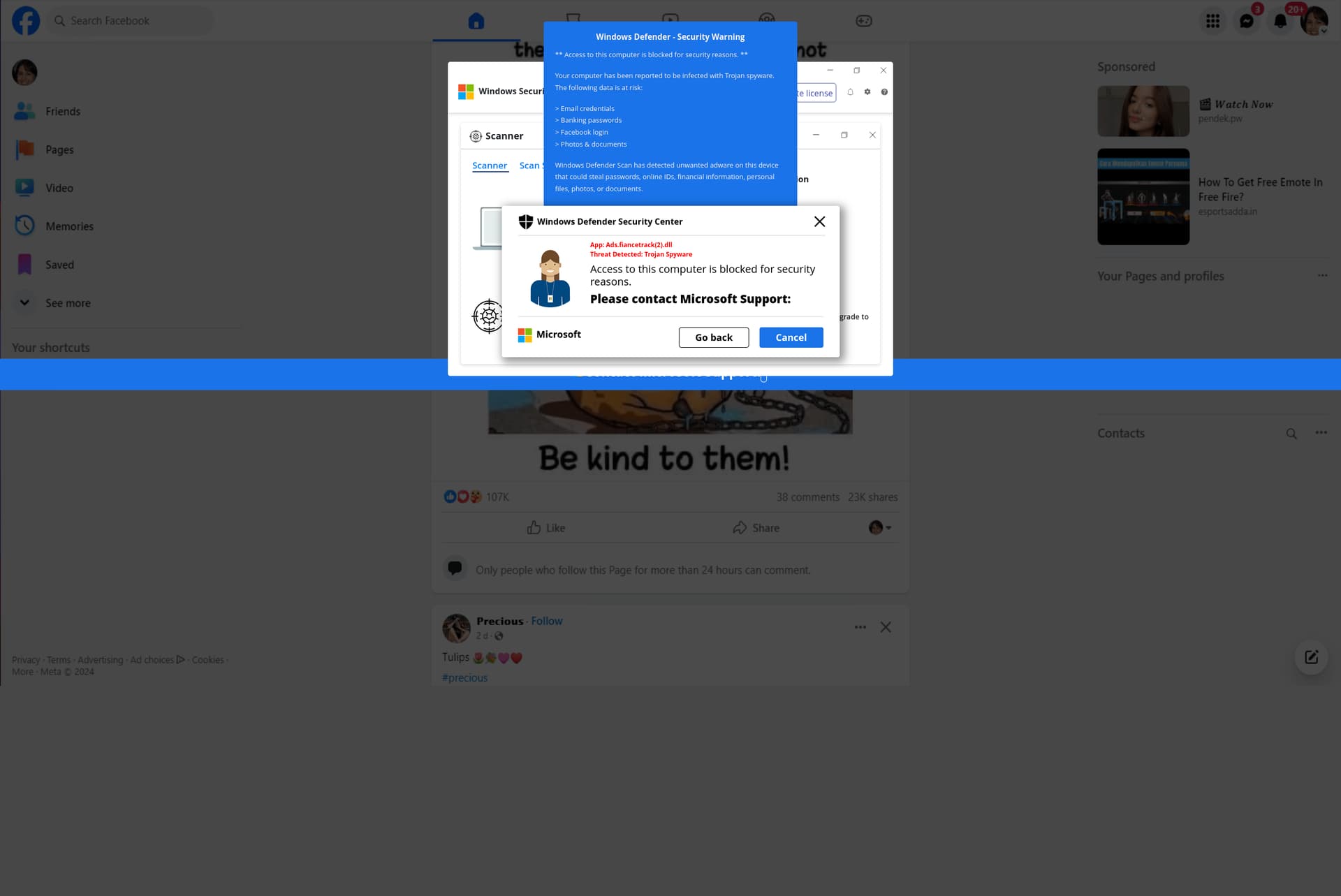
Detection
The .autos zone is currently ranked third on Netcraft's anti-rating and this scam campaign utilizes the .autos TLD. However, upon closer inspection, the following details become apparent:
Title: Facebook
Favicon: No favicon
ASN: AS14061 - DIGITALOCEAN-ASN, US
TLD: autos
Registrar: Namecheap
Upon investigating the root of the domain, we are greeted with a 403 error from nginx, which is actually a favorable outcome for our investigation. Leveraging urlscan, I was able to get a list of sites with similar templates. Given that they all resided in the autos zone and shared a comparable path structure, it was reasonable to infer that they all originated from the same author. This insight enabled me to identify unique paths directly linked to this tech support scam campaign. Here is a comprehensive list of those paths:
/rebalancing/spoke/
/stickers/nation/
/serene/dune/
/dale/creek/
/epsilon/bravo/Fortunately, the site does not verify the presence and/or value of parameters in the URL, which significantly narrows down the number of potential link combinations for the final check. This oversight on the part of the scammers simplifies our task of identifying malicious links.
With access to zone files in the autos zone, obtaining a list of actual unique domains was straightforward. Initially, I had to sift through 42,785 possible domains. After resolving the domains, 41,260 with A records remained. Further scanning reduced the list to 19,756 domains that responded to my scan. This significant reduction was encouraging and helped narrow down the search. Upon closer examination, I discovered that this campaign utilizes AS14061, which is owned by DigitalOcean, and the servers are located in the USA. At this juncture, I could have used the IP to ASN database from ipinfo to minimize the list of domains for bruteforcing paths. However, I wanted to confirm if a single provider was used throughout this operation, which was indeed the case. I filtered the scan results to include only those domains that did not return any favicon, returned a 403 error on the main page, and had a title of "403 Forbidden". This filtering yielded a list of 1,330 domains that met my criteria. After bruteforcing the paths specified earlier and sorting by code 200 and the title "Facebook", I was left with only 223 domains. Further verification confirmed that the A records of these domains belonged entirely to AS14061. It's worth noting that there were no fixed IP addresses, and they changed quite frequently. In total, there were 54 active IP addresses associated with the 223 active domains, the list of which is provided below. This operation was not a one-time occurrence, and each time I performed it, the number of discovered domains remained high. Over a period of 10 days, I managed to identify 382 malicious domains.
Conclusion
Since the domains of this particular threat actor were registered through Namecheap, which promptly responds to complaints, all of these domains were disabled within 24 hours of filing a complaint. However, threat actors continue to register new domains on a daily basis using Namecheap.
IOC:
128[.]199[.]0[.]60
137[.]184[.]115[.]237
137[.]184[.]182[.]89
137[.]184[.]185[.]3
137[.]184[.]91[.]223
137[.]184[.]9[.]39
139[.]59[.]194[.]231
139[.]59[.]220[.]40
143[.]110[.]225[.]217
143[.]110[.]232[.]134
143[.]110[.]232[.]83
143[.]198[.]97[.]240
144[.]126[.]217[.]117
146[.]190[.]120[.]128
146[.]190[.]121[.]232
146[.]190[.]174[.]196
146[.]190[.]202[.]232
146[.]190[.]35[.]108
146[.]190[.]43[.]49
146[.]190[.]52[.]72
146[.]190[.]59[.]179
146[.]190[.]63[.]24
147[.]182[.]196[.]35
147[.]182[.]226[.]0
147[.]182[.]249[.]7
159[.]223[.]193[.]222
161[.]35[.]237[.]50
164[.]92[.]105[.]194
164[.]92[.]109[.]164
164[.]92[.]115[.]133
164[.]92[.]120[.]214
164[.]92[.]75[.]117
164[.]92[.]75[.]82
164[.]92[.]81[.]111
165[.]232[.]141[.]144
165[.]232[.]143[.]180
165[.]232[.]153[.]34
24[.]144[.]86[.]151
24[.]144[.]95[.]55
24[.]199[.]109[.]69
24[.]199[.]96[.]208
45[.]142[.]246[.]128
64[.]23[.]129[.]19
64[.]23[.]153[.]75
64[.]23[.]154[.]191
64[.]23[.]157[.]50
64[.]23[.]158[.]92
64[.]23[.]180[.]97
64[.]23[.]192[.]43
64[.]23[.]193[.]56
64[.]23[.]204[.]64
64[.]23[.]212[.]199
64[.]23[.]214[.]108
64[.]23[.]220[.]179